What is a Virtual Private Network (VPN)?
A VPN creates a secure tunnel which allows the user to send and receive data over the internet to another network as though they are directly connected to that network, often this tunnel is encrypted to ensure that your data can not be read as it travels across the network.
Many are likely to be familiar with a client to site VPN which is often used to allow remote workers to connect to a network such as their work office without having to physically be at the office and connect using a network cable or Wi-Fi. This technology has enabled people to work away from the office whilst still having access to the networked resources which they would have should they be physically present at the office and on the network, essentially they are virtually connected.
For a VPN to work, the user utilises their existing internet connection and creates a tunnel usually but not exclusively, by signing into a portal which then creates a connection to the server, once the tunnel is created the user's Internet Protocol (IP) address would change to that of the VPN server.
It is paramount that the tunnel is encrypted to prevent anyone from being able to see what data is transmitted from the client to the server, there are a number of protocols and encryption standards which can be used to ensure a secure tunnel, not all encryption are equal and some should be avoided entirely.
For the sake of this article and brevity, I am going to put the use of VPN’s into two different use categories; the first being client to site VPN for remote working and the second being the heavily marketed VPN for the everyday internet user.
Marketeers rely on people to delete, distort and generalise the information which they receive to sell their products and services. Hearing this same message from various providers entices then addresses fear, resulting in many concluding that they must use a VPN or they will be a cybercrime victim. Read ten VPN providers advertisements and it is of no surprise that this is the message that people receive. Here are some keywords that a few providers are promising; strongest VPN security features, great for security and anonymity, anonymous torrenting, no-logs policy and secure core servers.
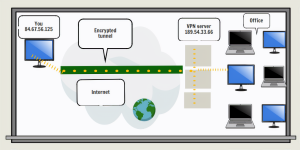
Here we can see how data travels over the internet to a work office when a VPN is used.
Who Should Use a VPN?
VPN’s have been as equally revolutionary for a distributed workforce as Wi-Fi has been for the nation. Those whose jobs involve working away from the office may be familiar with working from the airport or hotel room but the recent pandemic has forced the traditional desk worker to become just as familiar with the technology at a much quicker rate. Any person wishing to be able continue to work away from a fixed network should employ the use of a VPN, if they haven’t been forced to do so already.
Before the nation was forced to become a distributed workforce, many had been using VPN’s for their own personal reasons. The same protocols and encryption are used for these VPN’s therefore they are no different, it is their employment and intended use which is different. Many providers market these VPN’s as a method of staying safe online, preventing cyber-attacks and keeping your data private. Whilst the many marketing points are not necessarily a lie if no context is given, they are not holistically true either.
Lets take a look at some of the reason why people choose to use a VPN
The Distributed Workforce
The future of communal office desk work has been called into question now that the nation has been forced to work from home, Leeds City Council were able to have their 11,500 employees all working remotely over the course of a weekend proving that organisations of all sizes are able to do so. There is a proven business case for this use which will no doubt continue once we return to some form of pre pandemic normality.
Privacy
The decision to employ a VPN is likely a reaction to combat what a person perceives as a threat and what value they place on that perceived threat. Privacy is likely to be the top of most people’s priority list which allows marketing experts to cleverly tailor their advertisements to satisfy this fear by selling a VPN as a way of maintaining privacy online.
Internet Service Providers (ISP) are well known for collecting their customer's data and tracking their behaviour which is then used to enhance their services and is often sold onto thirds parties, read the terms and conditions and it will state how your data is used although often described in a misleading way. You do have the ability to request your data to be deleted however ISP’s are forced to retain certain information due to the Investigatory Powers Act 2016.
A VPN provider’s sales pitch focuses on this issue of (ISP’s) collecting, using and selling your data as a way of selling their services and products.
When using a VPN, your ISP can still see your IP and the VPN server IP but they cannot see the contents of the packet (data) as it travels from your device to the VPN server as it is encrypted. This means they know you are using VPN but don't know what sites you are visiting beyond that. Privacy should not be confused with anonymity, government authorities often force VPN providers to hand over the logs of their servers as happened to Cody Kretsinger of Lulsec who used Hidemyass.com to launch attacks against Sony, NATO, SOCA, and 77 law enforcements sheriff websites.
This particular provider came under scrutiny from its users as to how it was able to hand over this information. Hidemyass.com later said “We have had a few queries as to our logging policies. We only log the time you connect and disconnect from our service, we do not log in any shape or form your actual internet traffic”. There are various types of logs which are kept by the providers, anything other than not collecting logs at all is reason to find another provider.
The EU’s article 28 (GDPR) recommends removing personally identifiable information from any sensitive databases, only it may not be enough to protect the owner of that information as a study by Luc Rocher, Julien M. Hendrickx & Yves-Alexandre de Montjoye states “99.98% of Americans would be correctly re-identified in any dataset using 15 demographic attributes”. The article can be found at: https://www.nature.com/articles/s41467-019-10933-3
Many providers say they are not keeping logs or delete logs within a certain time period however reading the terms and conditions may actually reveal they are misleading the reader. Aside from the provider, there are other groups who have an interest in acquiring your data. Individual hackers, advanced persistent states and our own government organisations are all known to target servers. If I was looking for criminal activity, I would probably start with a VPN server; it seems logical that some people use VPN’s to try mask their identity and believe they are anonymous by using a VPN. History has taught us that if you are using a VPN for criminal activity then you will be caught, make the world a more harmonious world and use your skills for a greater cause.
Due to the leaking of NSA documents, we know that the PRISM programme was responsible for forcing ISP’s into handing over their logs to the NSA. It likely that you are not concerned about the government from acquiring your data and you are more concerned about your data being harvested, something which is guaranteed from your ISP and just as likely if using a VPN. Ensure you read the terms and conditions thoroughly and understand what they mean by personal data. They may not regard your IP and cookies as personal data. For an in-depth analysis of 123 VPN logging policies take a look at Aimee O’Driscoll’s article at https://www.comparitech.com/vpn/vpn-logging-policies/
Cheaper Deals
We may be familiar with the price discrimination between the north and south of the UK, where the same product often costs more the closer to London you are. The same applies throughout the world, something you may have experienced when buying from overseas or whilst abroad. Some sellers refer to it as an idiot tax, a derogatory reference to the buyer being unaware of what the true cost of the product or service should be.
The same discrimination applies when buying online however the circumstances are different. With some VPN providers it is possible to choose the location of the server which you connect to therefore the IP address changes. Providing you do not have any browsing history on your device then the site which you are purchasing your product or service from can only assume that you are buying from the location of your IP. Surfshark diligently put this to the test and proved their theory in seven different scenarios. The article can be found at: https://surfshark.com/blog/6-ways-to-save-money-with-a-vpn
Geo-Spoofing
It is possible to give the impression that you are physically at a different location than you are by imitating another IP. Various sites have geo blocking policies which restrict certain access to their content, this is often evident when confronted with the message ‘sorry, this site is unavailable in your location’. Most VPN providers allow you to choose which location you wish to connect to thereby changing your IP to that location and bypassing geo blocking policies.
Sporting fans are able to watch their favourite team play anywhere in the world and gamers can enjoy their games before they are released in the UK. By using the same overseas server as the people they play, the UK player can avoid latency issues as well as paying the same prices, perhaps even benefiting from the differing strength of currencies.
There are more significant personal safety reasons why some may use geo-spoofing such as those who live in communist countries where certain applications are restricted. The Communist Party of China has blocked approximately ten thousand domain names under is censorship policy; Reddit, DuckDuckGo and YouTube are to name a few which may of us take for granted in a democratic society, the majority of VPN’s are also blocked.
In 2011 The Tunisian government performed a Man in The Middle (MiTM) attack on Facebook users connecting from within the country by capturing their login and passwords. In this case, a VPN would have protected them against this attack providing the VPN server was located overseas and the Tunisian government did not have access to the server.
Public Wi-Fi
Many people connect to public Wi-Fi regardless of the fact that everyone else on the network can connect to their device and are able to carry out nefarious activity as well as see their traffic. Using a VPN in this situation will ensure that all of your traffic is encrypted as it travels over the wireless network so it cannot be read between your device and the VPN server, anyone watching will still be able to see your IP and the VPN server IP but not be able to see your data or the site you are browsing.
Connecting to an unknown wireless access point also entails other concerns as you cannot be sure that the device is not owned and operated by a villainous character. The Service Set Identifier (SSID) can be changed to match that of a trusted Wi-Fi access point in the same area, leaving a victim to unknowingly connect to what they think is a safe access point.
Summary
By all means use a VPN, you will be a little better off using one than not, choose your provider carefully and understand what you are purchasing. Assuming you have chosen to use VPN for privacy, then you may well just be paying extra for a second ISP and for somewhere to store your data, an ISP who is still harvesting your data and making even more money from you than your monthly subscription. Read the terms and conditions of the VPN provider and also the terms and conditions of the site where are acquiring your recommendations from, any evidence of affiliate links on the recommendation site to VPN providers then disregard their information.
VPN’s are not as effective on mobile phones due the way that phones connect to cell towers. Your location would still be visible to the cell tower, not to mention that many applications including Google Maps triangulate your real location using your phone’s GPS location, employing a VPN will not change your true location.
Not all VPN’s provide strong encryption with some offering a service with no encryption at all, if something is free then look into the reason why. Not all encryption is equal either, there are some which have been broken and are still in use. Some providers don’t advertise their encryption standards but where possible look for:
• Minimum 128 bit encryption key
• Dependable Key exchange
• Strong ciphers such as AES,
• Strong HMAC authentication
VPN’s are often sold as a one stop shop method of keeping you cyber safe and disregard the many other attack vectors which are the cause of personal security breaches on a daily basis. Five areas where people can help secure themselves much better than a VPN are:
• Poor password policy: Spotify, PayPal, Facebook are just a few of the accounts which people report to have been breached on a daily basis, often as a result of reusing credentials. Use complex passwords, don’t recycle them.
• Phishing attacks: Unless a user has undergone phishing training then they are very likely to click on a malicious email, only slightly more likely than if they had undergone awareness training. Humans will always be the weak link in our cyber armour.
• Unsecured websites: It would be very difficult to assess the security of every site before you visited it. Security flaws which you have no control over can results in your security being breached. Even if a website is secure, websites are built to capture the users activity as well as track the site you came from.
• Malware: Either as a result of clicking on a malicious email, from browsing a malicious website or from downloading a malicious file.
• Internet of Things: What better for a hacker than for someone to put a weak internet facing device on their network to help you gain access, probably still using the device default credentials which can be found online.
A VPN is not going to help against any of the above threats, or against the plethora of threats which are in your mind right now. Don’t assume that you are secure by giving away a subscription fee to a VPN provider who may or may not be selling your data to the highest bidder. Cyber security requires a holistic and continuous methodology which can’t be solved with a one off purchase, at least not yet anyway.
VPN’s do not always provide complete anonymity. If anonymity is what you are looking for then the closest you will get is The Onion Router Project (TOR), used correctly it is an amazingly powerful tool, used wrongly then the end of humanity is not far away. For some, the use of TOR is the only way they can have freedom of speech without suffering dire consequences.For more advice and guidance please get in touch