Among the increasing threats within the cyber world, malware, keyloggers, and backdoors stand out due to their potential to cause significant damage. Without a proper incident response plan in place, these threats can cause severe problems for anyone affected, and the consequences can be even more worse.
Grasping these threats and knowing how to counteract them is essential for helping to ensuring security for any business.
What is Malware?
Malware (malicious software) is a broad term that contains various types of harmful software designed to disrupt, damage, or gain unauthorised access to computer systems. Common types of malware include viruses, worms, trojans, ransomware, and spyware. Malware can steal sensitive information, encrypt files, disrupt system operations, and more.
Types of Malware
Virus: Attaches itself to legitimate programs and spreads when these programs are executed.
Worm: Self-replicates and spreads independently across networks.
Trojan: Disguises itself as legitimate software but performs malicious activities once installed.
Ransomware: Encrypts files and demands a ransom for their decryption.
Spyware: Secretly monitors and collects user information.
What is a Keylogger?
Keyloggers are a specific type of spyware designed to record keystrokes made on a keyboard. They are used by cybercriminals to capture sensitive information such as usernames, passwords, credit card details, and other confidential data. Keyloggers can be hardware-based or software-based.
Types of Keyloggers
Hardware Keyloggers: Physical devices connected to the keyboard or built into the keyboard itself.
Software Keyloggers: Programs that run in the background, capturing keystrokes without the user's knowledge.
Software-based keyloggers are often equipped with rootkit functionality, allowing hackers to hide within a system, track user activity, save data, and forward it to other cybercriminals. These keyloggers can also monitor clipboard activity, location data, and even microphone and camera inputs.
Keylogging software operates at various levels:
Kernel Level: These complex keyloggers operate at the core of the operating system, making them hard to diagnose and remove. They have deep access to the system, essentially controlling the device.
API Level: The most common type, these keyloggers intercept signals between the keyboard and the application, functioning like a recording device between the physical keyboard and the on-screen application.
Screen Level: Known as "screen scrapers," these keyloggers take regular screenshots of the display.
Browser Level: These keyloggers, though less complex, are still dangerous. They record inputs in web forms, capturing sensitive data like login credentials and Social Security numbers.
Software-based keyloggers are more prevalent than their hardware counterparts due to their discreet nature and ease of distribution as malware. However, hardware-based keyloggers remain a significant threat.
Hardware-Based Keyloggers
Hardware-based keyloggers involve a physical component and cannot be detected by antivirus software since they are not installed on the computer. These keyloggers use their internal memory to store and encrypt data. Types of hardware-based keyloggers include:
Keyboard: Installed within the wiring or directly inside the keyboard.
Physical Drive: Delivered via USB drives or Mini PCI cards.
Third-Party Recording: External devices like strategically placed cameras to monitor keyboards or keypads.
Acoustic: Rarely used, this method records the distinct sounds of keystrokes.
Although less common than software-based keyloggers, hardware-based keyloggers can still pose serious risks to data security.
What is a Backdoor?
A backdoor is a method of bypassing normal authentication or encryption in a computer system, network, or software application. Backdoors are often installed by cybercriminals to gain unauthorised access to systems and maintain persistent control over them.
Malware is quite regularly used by threat actors to create an entry point into the system. When the malware infects the system, it facilitates the installation of other malicious programs, enabling the creation of a backdoor. Once the backdoor is in place, hackers can send commands from a command-and-control server to steal data or damage the system.
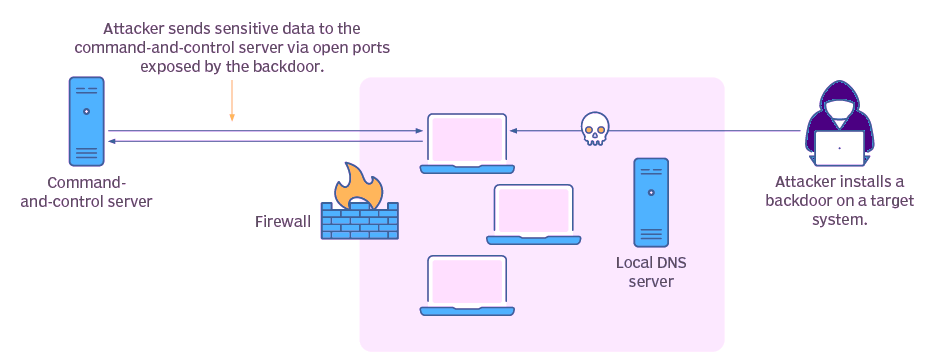
Backdoor attacks typically remain undetected initially because hackers do not forcefully breach security systems. Once they have remote access to a network or device, they can install malware, steal data, and monitor user activity without causing immediate disruptions.
Types of Backdoors
Generally speaking, there are two types of backdoors:
Operating System Backdoors: Exploits vulnerabilities in the operating system. This enables hackers to find and exploit an existing backdoor within a system to provide unauthorised access.
Application Backdoors: Hidden functionalities in software applications that allow bypassing security controls. In this way the hackers install a new backdoor themselves.
A backdoor attack can occur in two primary ways. Hackers may either find and exploit an existing backdoor within a system or install a new backdoor themselves.
In the first case, hackers use the backdoor to bypass normal security protocols and gain unauthorised access to a computer system and its data. In the second example, they exploit system vulnerabilities to infiltrate the system and implant backdoor software. Once installed, the backdoor allows attackers to re-enter the system at will, even if the original vulnerabilities are patched.
Preventive Measures
In the following sections, we highlight ways in which to help prevent malware, backdoors and keyloggers.
Against Malware
Install Antivirus Software: Use reputable antivirus software to detect and remove malware.
Keep Software Updated: Regularly update operating systems, applications, and security software to patch vulnerabilities.
Use Firewalls: Enable firewalls to block unauthorised access to your network.
Be Cautious with Downloads: Download software only from trusted sources.
Educate Users: Train employees and users about the risks of phishing and other social engineering attacks.
Against Keyloggers
Use Anti-Keylogging Tools: Implement software designed to detect and block keyloggers.
Enable Multi-Factor Authentication (MFA): Adds an extra layer of security, making it harder for keyloggers to capture all necessary information.
Monitor for Unusual Activity: Regularly check for unusual activity on your accounts and systems.
Against Backdoors
Conduct Regular Security Audits: Regularly audit your systems for vulnerabilities and unauthorized access points.
Implement Strong Access Controls: Use strong passwords and limit administrative privileges to essential personnel only.
Use Intrusion Detection Systems (IDS): Deploy IDS to monitor network traffic for suspicious activity.
Response Measures
Unfortunately, sometimes, even the most secure of businesses may find themselves facing a cyber security incident. Incase of this happening, it’s always important to be aware of the response measures to take when malware, keyloggers, or backdoors are detected. These preventative strategies are essential for effective incident response, helping to mitigate potential damage and restore system integrity.
If Malware is Detected
Isolate the Infected System: Disconnect the system from the network to prevent the spread of malware.
Run Antivirus Scan: Use antivirus software to identify and remove the malware.
Restore from Backup: If necessary, restore the system from a clean backup.
If a Keylogger is Detected
Disconnect from the Internet: To prevent further data transmission to the attacker.
Identify and Remove the Keylogger: Use anti-malware tools to locate and remove the keylogger.
Change Passwords: Change all passwords that may have been captured.
If a Backdoor is Detected
Identify the Source: Determine how the backdoor was installed and address the vulnerability.
Remove the Backdoor: Use security tools to remove the backdoor.
Strengthen Security Measures: Enhance security protocols to prevent future backdoor installations.
How can you make sure you’re protected?
Today, understanding the threats posed by malware, keyloggers and backdoors is essential to protecting individuals and organisations. These malicious entities can cause serious harm by stealing sensitive information, disrupting operations, and giving cybercriminals a break in.
Even with strong preventive measures, cyber incidents can still occur. This is where the importance of a well-defined incident response plan comes into play. Effective incident response is critical for rapidly cleaning up infected systems, running antivirus scans, and restoring from clean backups. Addressing known keyloggers and backdoors immediately can prevent further damage and unauthorised access.
Incident response not only helps reduce the immediate impact of cyber threats but also helps identify vulnerabilities that can be strengthened to prevent future attacks Adapting incident response strategies regular and employee training to recognise and respond to security breaches are important components of a comprehensive cyber security strategy.