Stealing my CEO’s Identity
Recently we were issued some very flash, and eye wateringly pricey, new NFC business cards purchased from V1CE :

Whilst they turned out to be not quite as useful as we had hoped they would be (it’s actually a bit of a faff sharing details if someone doesn’t have NFC enabled on their phone and they wouldn’t read all of the time), I thought I would have a quick dive down into how they worked and if there was anything interesting about them from a security perspective.
I mean the website says it’s secure – so I’m sure it is …

Sitting mine on my Proxmark RDV4 shows that it is probably a Mifare ultralight/hospitality or NTAG 2xx :
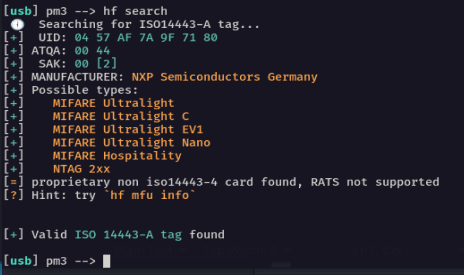
Turns out that it’s a NTAG 213 – a common inexpensive tag that costs less than €0.50. Given that these cards can sell for up to £100, they must have made sure some of that profit was invested in securing the card surely?
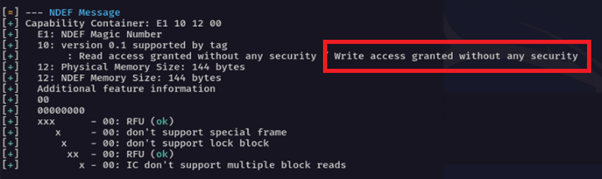
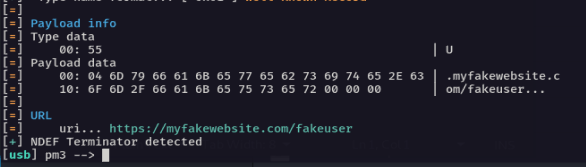
Grabbing some more info on the card showed that it appeared possible to write to the card without any security. Now, this is where things started to get a little bit interesting :
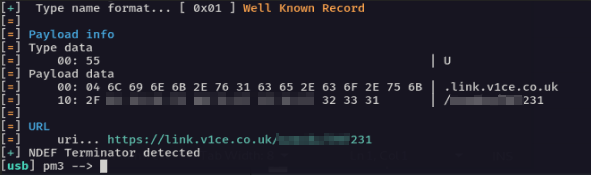
The card just gives you a standard NFC Data Exchange Format (NDEF) payload of a URL. Visit the URL given and it takes you to a web page listing all of your contact details and the opportunity to download them as a Virtual Contact File (VCF) :
Which will take you to here :
Since I can write to the card, I can change the link and the VCF file that is downloaded.
In other words, once I have got close enough to the target card, I can rewrite the data, and every time that card is presented to someone new, they will get the data I chose to populate it with rather than the data the card owner believes to be on there. Logging onto the V1CE account and changing details won’t make any difference as the card will no longer send someone to the V1CE page but instead to my page. The only way to fix the issue would be to rewrite the card.
So let’s see if I can wangle myself a quick promotion :)
Firstly we need to create a website that will host the details and create a personalised VCF file for download. A few quick clicks later and we have a perfect clone of the website and need to update the details :
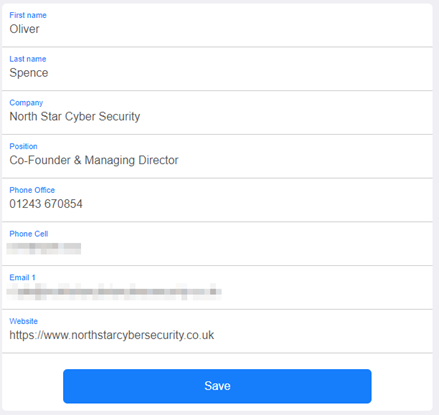
Next, update the target card. All we need to do for this is overwrite the existing card with the same details we create. It takes less than 10 seconds to do this :
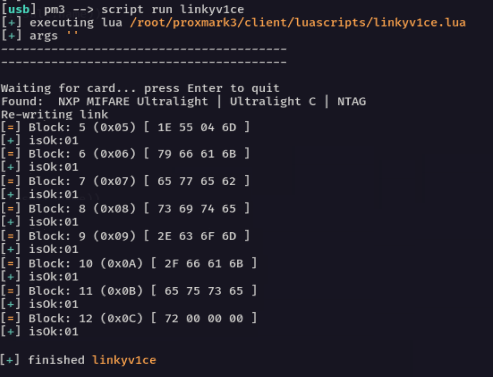
With an external battery attached to the Proxmark it can be used when not attached to a PC. It can even be managed from your phone through an optional Bluetooth addition. Writing a quick (and extremely ugly, hence not including it here) script for the Proxmark meant that it was possible to wait for a card to be presented and then discretely rewrite the target card in a matter of seconds once it was possible to get close enough to it with no suspicious cables :

It didn’t take long before we got the first hit :

Obviously, in this instance we served up the correct VCF file with the MD’s correct details. This is a research piece, not a resignation letter after all! His card is now returned to the correct settings.
However, if I had registered a similar sounding domain name and changed the mobile number, that contact would have my details and would be emailing and calling me, believing me to be Ollie.
Now, this is all well and good if you have expensive equipment like the Proxmark to do this with. You’re probably already relegating this to the realms of an edge case attack – requiring fancy hardware and all the planets to align for it to work. Well I wouldn’t be so quick to do so - you can do this from your phone with a piece of free software. The screenshots below are from NFC Tools Pro, but the free version supports writing to the V1CE card as well :
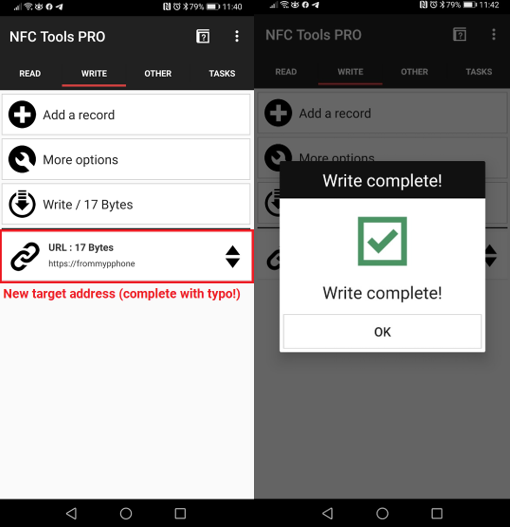
And checking the write was successful :
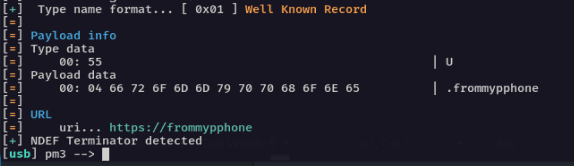
The best bit about this is your target will literally hand you the card and since these cards can be a little bit of a faff to use, it’s completely understandable that you have it for the second or two required to do execute the attack.
When looking at fun, flash new technology, it’s worth taking a moment to understand the issues surrounding them. This was a simple piece of fun, but it is worth understanding how it can be abused. Whilst this was a very targeted attack, there is nothing stopping someone from going to a trade show and wandering around rewriting all of these vulnerable cards. You only have to overwrite a single byte on the card to redirect all of the traffic to your domain. The link provided on the card by default is link.v1ce.co.uk, however if you were to overwrite the first . with a y for example, all traffic would be directed to linkyv1ce.co.uk :
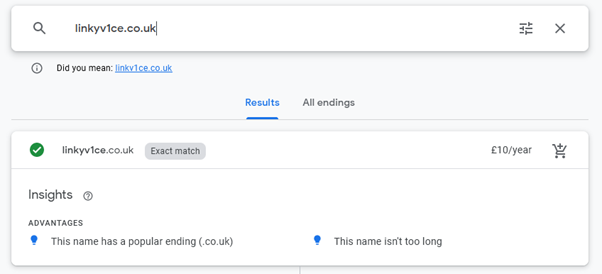
Which is available to register (at the time of writing). Set up your website on linkyv1ce.co.uk to mirror the link.v1ce.co.uk website and start tracking everyone whose card you’ve manipulated. Soon enough you’ll see someone important enough to not deliver the link.v1ce.co.uk content to, but your own.
What is the impact of all of this?
You could :
• Redirect the recipient to a site hosting malware.
• Redirect them to a competitor’s site, complete with a huge introductory discount.
• Reputational damage – what if every time you presented it the recipient was directed to an extremist site (or worse)?
• Easily impersonate the card owner.
Ultimately just be aware that when you are handing over your V1CE card, you might not get it back the same way you had it, and that could be for the worse. And if you’re not storing it in a shielded wallet, you don’t even need to get it out for it to be rewritten.
Just because it’s expensive and flashy doesn’t always mean it’s secure.