Ships to Scripts - How to be a Penetration Tester
Becoming a Penetration Tester in 18 months with no previous experience
In early 2019 I was teaching Royal Navy Radar Operators to be “fit to fight” anywhere in the world, my next Draft was quickly approaching. After completing 17 years of active service for my country, travelling the world, tracking missiles along the way. I carried out numerous roles, the most enjoyable being Operations Room Manager, but things had changed, I was no longer a young lad that wanted to go away for 6 months at a time. I have a wife, son and huge 78kg St Bernard at home, the time had come I had to leave the military, but what was I to do?
A good friend recommended cyber security, he said to me “you can make 60k easy, they have a massive shortage and you’re good on computers, join TechVets they will help”. When he said I was good on computers, what he meant was, I owned one and I liked technology, but how hard could it be?
I did some Googling and it appeared he was correct;
• The UK’s cyber security industry is worth an estimated £8.3 billion
• One small business in the UK is successfully hacked every 19 seconds
• There is a skill gap of 4 million professionals
• The average cyber security wage in the UK is 62k
• TechVets’ build a bridge for service leavers into cyber security
Note: The 60k mentioned by my friend can be misleading, as an entry-level you’re unlikely to make this, but given time if you’re passionate about cyber security it’s certainly achievable, with the potential to make even more depending on your chosen path and work ethic.
Ethical Hacker sounds cool right
So, with a quick Google, I subscribed to TechVets and joined their Discord channel. If you haven’t heard of Discord, it’s simply free software that allows you to communicate over voice, video or text.
I posted in the #transition group asking for guidance, I quickly received a reply from one of the members asking what area of cyber security I wanted to work in and what was my experience? He went on to explain;
• Preventing attacks
• Carrying out the attacks
• Cyber Threat Intelligence. Building up knowledge of existing or potential threats
I did some open-source research, there were so many options, but I knew straight away I wanted to be on the Offensive Team. The job had various titles such as Pen Tester, Ethical Hacker and White Hat. I liked the sound of the job, “finding and exploiting vulnerabilities”. I realised there were a lot of elements to it including, but not limited to Network Infrastructure Testing, Web App Testing and Wireless Testing. Then there was a social engineering aspect, manipulating people to divulge confidential information. I liked the sound of it, where do I start?
TechVets stepped in, one of the perks of being a member is a veteran version of Immersive Labs, which is an online technical training platform. After another conversation on Discord, I signed up for a free account, this gave me a taste of what it would be like to be a Pen Tester.
I am a kinesthetic learner, hands-on is where I learn and the platform allowed me to do that. It didn’t take me long to work my way up the leaderboard, currently ranked in the top 3%. I didn’t know how much I liked problem-solving, but now the prospect of hacking my way into a Network that was supposedly airtight sounded very appealing, I knew then this was the career for me.
Study Time
With my heart now set on getting into cyber security, I looked into what skills I needed. I already had some and you will too, most of them can be summed up as soft skills but don’t let the term soft demean them. Public speaking, effective communication, self-motivation, ability to work under pressure, problem-solving and report writing are just some of the transferable skills that I gained through the military. Though it was clear I was missing general IT and this was before I even started with the practical skills required to be a Pen Tester. So, under the recommendation of TechVets I started to learn the foundations of IT infrastructure.
Note: Below is a snippet of the TechVets generic starter path.

Five months later following some late nights, I had gained the knowledge of CompTIA A+, Network+ and Security+. I sat and passed the exams for the latter two with the help of Professor Messer on YouTube and by researching the Official Exam Objectives that are freely available on the CompTIA website. I was told the certifications aren’t essential, knowledge is key, but I figured being able to present the qualifications to a future employer won’t hurt.
Now I know about Network Infrastructure, Security, Common Attacks, Threats, Vulnerabilities, Architecture, Risk Management, CIA triad, Cryptography, Public Key Infrastructure (PKI), Configurations, Troubleshooting, Common Command Line Interface (CLI) Tools, to just name a few.
It was time to have some fun! I was missing the practical element. I downloaded Kali Linux, which is a free powerful Operating System designed for Pen Testers, it comes with over 600 security tools including Wireshark, Nmap, Aircrack, Msfconsole and Burp Suite. I started to use as many as I could, I got back to Immersive Labs, joined Cybrary.it, downloaded VulnHub boxes, launched OWASP Juice shop, bought some highly rated cheap courses on Udemy and subscribed to Hack the Box (HTB), all of which are practical learning platforms for IT enthusiasts.
Note: Cybrary.it no longer has as much free content, they only thing I paid for are the exams with the use of Standard Learning Credits (SLC), HTB VIP and a few Udemy courses that cost less than £20. I wouldn’t promote paying for anything else, although I’m not saying there aren’t other useful subscriptions but do your research before spending your hard-earned cash.
For me, HTB was the hardest and most challenging but it taught me so much, I hacked my way in with the help of Google and signed up for VIP, at first it was overwhelming but I stuck with it and by following the guides for retired boxes, I am now at the rank of Hacker completing live boxes which contain similar Common Vulnerabilities and Exposures (CVE) you come across in the field.
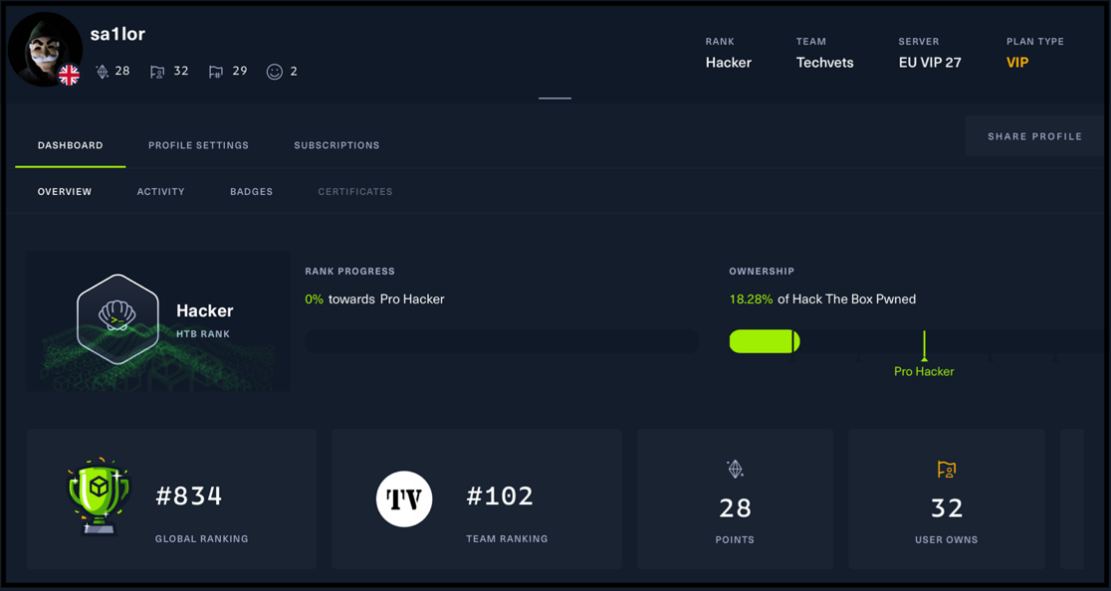
Note: With all these learning platforms take notes as you go, you will use the skills again.
Late nights
In February 2020 I left the RN to take up employment as a Maritime Technical Warfare Consultant, it wasn’t necessarily the job I wanted to do but it worked out well, the wage was good, I built on my previously mentioned soft skills and I could study in the evenings.
My spare time was now focused on the specific skills required to be a Pen Tester and achieving some more certifications to prove it. My chosen path was with CREST, which is a highly regarded international accreditation and certification body. For those looking to take the same path, it has two elements;
• Theory - CREST Practitioner Security Analyst (CPSA)
• Practical - CREST Registered Tester (CRT)
For CPSA I did the same as before, I downloaded the Official Objectives and went through them one by one, in my opinion, the exam is as wide as the ocean but not very deep, you need to know a little about everything.
Unfortunately, COVID-19 delayed my progress as the exam centres shut down. However, it did give me extra time to study. When they reopened, I booked in for CPSA and with my face mask on I made my way to the local Pearson Vue Test Center and managed to pass the hardest Multiple Choice Question Exam I had ever taken.
Note: There are company’s out there that do a two week-long course for CPSA and CRT, they can be used as part of resettlement, I was doing contract work but would recommend doing this if it works for you. Open-source study for CREST exams aren’t easy, they have a strict NDA so at times it was painstaking going through the Objectives. I know some will be reading this thinking of the recent CPSA leak, for me it’s disappointing after putting in so much effort to pass the exam, but I feel assured any cheaters will fall short in the long run.
Interviews
Although I hadn’t sat CRT, I felt I was ready to start applying for jobs. I had a home lab set up and could do things such as own Domain Admin with Windows 2010 Anti-Virus turned on, I was completing boxes on HTB with little or no prompt and was moving away from automatic tools like Msfconsole, because it was getting easy, I wanted to see the code and understand the methodology.
So, I started applying for Pen Testing Jobs.
Note: Before I sent out my CV, I used the TechVets CV service. I won’t go into the details but it’s very useful.
When you get to the stage of apply for jobs in cyber security, you will know many of the listings are after extraordinary requirements and certifications, entry-level jobs with CISSP, OSCP and 10 years’ experience, ok… that might be an exaggeration but you get the gist. I would still apply and sell the skills I had, highlighting what I achieved just by studying in my spare time.
It didn’t take me long to get an interview and secure a place with a pro ex-military, very reputable and highly regarded company, Cybaverse. I will be sitting CRT soon and Offensive Security Certified Professional (OSCP) later next year with the long-term goal of achieving Certified Information Systems Security Professional (CISSP), I know with the passion I have for cyber security that I will succeed.
Conclusion
I titled the blog Ships to Scripts, I don’t want this to put anyone off, you don’t have to know a programming language going into Pen Testing, I didn’t, you have all the above to learn first, but scripts are what control the tools we use. You will start to write your own, enabling automation or editing to allow for better functionality and it won’t be long before you’re taking on more study, I would recommend starting with Python.
The biggest takeaway point I can offer is… if you enjoy it, do it, give it your all and it will give back.
About the Author
I’m Michael Jepson aka sa1lor. I hope you found the blog useful feel free to connect with me on LinkedIn, Networking shouldn’t be underestimated, I am more than happy to offer guidance where I can.
Note: I will leave you with this image of my previously mentioned pooch who is pleased I won’t be going away for any more 6 month deployments, the same might not be said for my wife having to listen to my dits about exploits I managed to carry out on HTB.

***If you are a Veteran, Service leaver or Reservist curious about a career in Cyber/Tech, come and join us for free at https://techvets.co/***