Is MFA as secure as you think?
Due to probability, sometimes an event is more likely to occur than we might have first thought. For example, large numbers can give a false sense of security over actual statistics. Recently at Cybaverse, during an engagement, this happened.
Despite the odds being one in a million, careful analysis of how the MFA was handled showed critical flaws in its implementation that could allow an attacker to brute-force the token in under 8 hours with a 100% chance of success.
You might be thinking, but you need credentials first, and I bet these were provided. If this is your mindset, for the sake of security, I would encourage you to reevaluate. Nothing is 100% secure, and something as trivial as a password is often easily obtained. On multiple occasions during Red Team engagements, employees have just passed them over when we impersonate IT support, and this is just one example of how they can be obtained.
So, we have credentials that align with best practice and MFA was enforced, which was pleasing to see. The MFA code was six digits giving 1 million possible combinations.
A simple test was conducted first to test brute-force protection, with a known code between 983,000-985,0000 which was accepted.
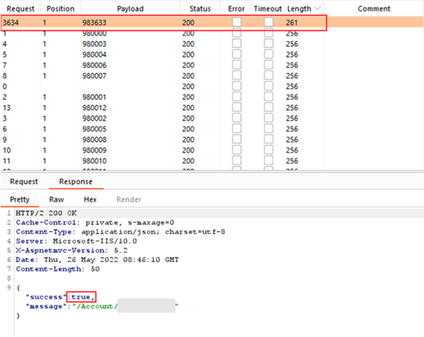
Further testing resulted in the server accepting approximately 20,000 requests per minute. However, after approximately 100,000 requests, the brute-force is hindered by a redirect to the original login page.
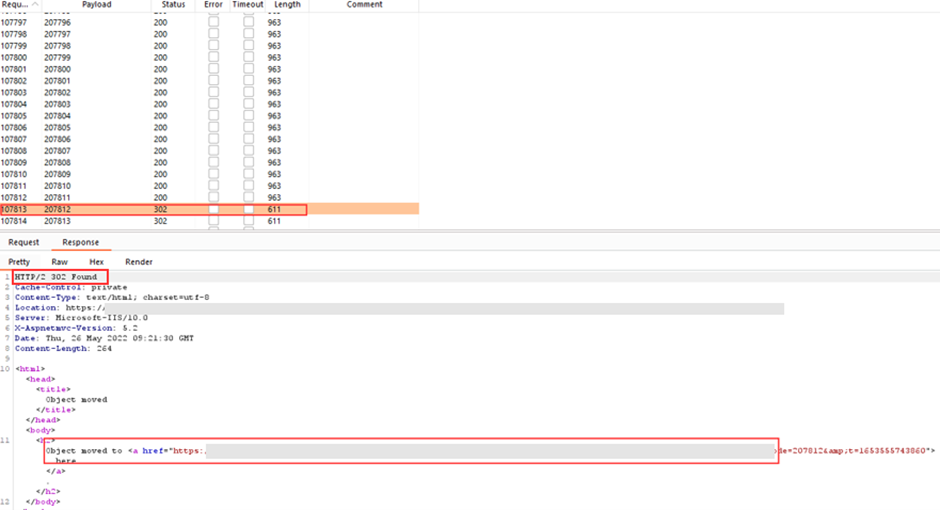
Some further enumeration concluded the cookie issued when providing valid credentials expired after 5 minutes. Still, the attack could be attempted again, log in and brute-force 100,000 numbers until the code was within the range.
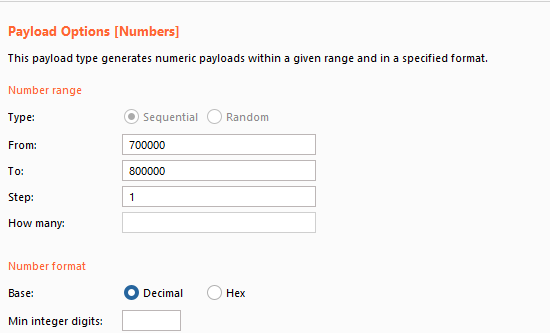
A Proof-of-Concept attack is shown below. An attacker could choose the range between 700,000-800,000. If it failed, reauthenticate until a code was issued within the set range.
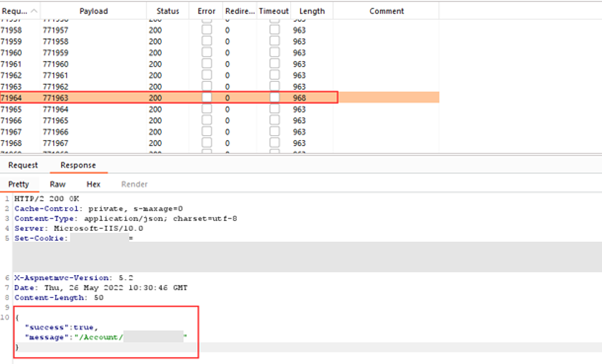
The attack would be successful once a code was within range.
Although based on probability, the chance of brute-forcing the code was a 1-10, for those of you who like your cyber with a side dish of stats and maths, you can calculate the probability of something of p probability happening after n tries using the formula 1-(1-p)^n.
So for this example, assuming a uniform distribution of the MFA code, we took a probability of 10% being the one in 10 chance of landing in the correct key space.
This gives the following data:
.png)
Or if you prefer your probability in the form of a graph:
.png)
The data above provides a more quantifiable success rate of attack;
Six attempts take 30 mins resulting in a ~ 50% chance of success.
Twelve attempts take 60 minutes (one hour) with a >70% chance of success.
Twenty attempts take 100 minutes at a ~ 90% chance of success.
Lastly, eighty-four attempts take 420 minutes (seven hours), providing a 99.99% chance of success.
A simple lockout policy, correctly implemented, is all that is required to mitigate this issue effectively. In under 8 hours, the probability of guessing the MFA code is 100% - this means an attacker could have access to the internal network overnight and have a couple of hours to embed themselves before the working day starts at 0900, and this is where defence in depth comes in.
If there was no lockout policy, how would you know that someone was inside your network? Is there monitoring in place for unusual activity on the network? Are sessions timed out after a period of time, forcing the user to log in again? Even if you could detect a malicious user internally, how will you go about evicting them effectively from the network?
Reliance on a single line of defence can be extremely risky.
Cybaverse recommends that you engage with your cyber security partner to get an overview of the risks to your organisation and what measures you can take to reduce them.