Remote Collaboration Software Security - If Your Name’s Not Down, You’re Not Coming In. Or Are You?
TL;DR
Video conferencing, group chats and similar collaborative applications are allowing the world to remain connected. Ensure that only those who you want to connect with on the applications are able to do so.
Key Take Aways:
• Familiarise yourself with the settings
• Don’t share screen shots of your meetings on social media.
Staying connected during the current situation is paramount for our health, not to mention the requirement for a distributed workforce to continue to collaborate. Had we encountered this pandemic at the beginning of the last decade then we may not have had the resources to communicate in the same productive way which we do today. Granted, we had the ability to text, call and email but they don’t quite provide the same level of interaction as the technology which is available at our fingertips as today.
Pandemic aside, many distributed workers would already be familiar with communication applications such as Zoom video conferencing, Microsoft teams and Slack as they allow video conferencing and instant chat among their many features. Unsurprisingly when face to face communication has been restricted, technology has been able to fill this gap and allow many teams to continue to work together as well as allow organisations to continue some form of routine and keep their staff employed in meaningful work. For many it has no doubt been a novelty to share our screens and join a virtual meeting from the comfort of our living room whilst still in our pyjamas with a cat laying at your feet, I for one noticed a lot of social media posts of people showing a screenshot of their virtual meeting with their colleagues all working from the comfort of their homes and gardens.
There is nothing wrong showing your social media network photos of your meetings etc, after all someone may see your post and not be aware that it is possible to use such mediums so effectively. This is the brilliance of platforms such as LinkedIn; I am constantly learning from other people by seeing what they are accomplishing and I find it inspiring when someone innovates to produce a better outcome despite the circumstances.
Sadly not everyone who views your Zoom or Microsoft Teams photo carries the same view, combined with some peoples boredom they may be looking for ways to entertain themselves by inventing a lockdown version of gate-crashing.
Whether you are discussing business details with colleagues, personal detail with parents or holding a virtual silent disco, it is likely that you would not appreciate someone joining in on your meeting. Certainly no one would want their children to be interrupted whilst catching up with friends or receiving lessons.
We will take a look at how you can stay secure whilst using collaborative applications using a recent example from the Government.
As the Prime Minister continues to lead the country from isolation, he is making full use of social media and video conferencing as can be seen from the picture below of his Zoom meeting which he posted on Twitter on March 31.
As the meeting was on going at 1120 on 31 March and the Prime Minister tweeted the photo at 1452 on the same day, it is unlikely the meeting was live when the photo was tweeted. However, there are situations where the meeting ID would continue to be valid after the meeting ended such as scheduling recurring meetings and using a personal meeting ID, this would allow further use of the same meeting ID. Assuming that the Cabinet Office holds these meetings on a recurring basis then they may have scheduled a recurring meeting which would mean it would be the same ID for the following meeting. For security, it is best to use an instant meeting as this ID expires when the meeting ends, personal meeting ID’s carry the same risks as a recurring ID as they are also reused.
Depending on what settings are enabled on Zoom then there may or may not be a 6 digit password required to join the meeting. The green padlock in the top left corner may be perceived as password secure to some, however it signifies that encryption is in use and not a password, a whole different subject which also has a great deal of coverage at the time of writing this article. Ensure a password is required and it is communicated from host to attendee via a secure method. There are numerous password settings available, further information can be found at the following link:
- Zoom: Advanced Security Settings
https://support.zoom.us/hc/en-us/articles/360034675592-Advanced-Security-Options
In the screen shot below we can see how to schedule a meeting with three important settings highlighted in yellow; Recurring meeting, Personal Meeting ID and Require Meeting Password.
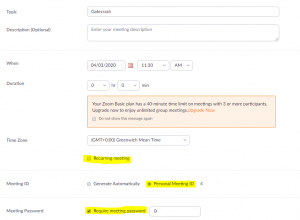
We can only speculate if the Cabinet Office had a password set and if so, how this password was communicated from the host to the attendees.
As we can see the Cabinet Office are part of the 73.3% of the UK who are using Wi-Fi, assuming their security awareness is of the same level as we see above then it would be trivial to intercept the password as it was sent to the attendees.Assuming it is sent via email, an attacker could position themselves within wireless adapter range of each attendee and intercept their home Wi-Fi packets, capture the handshake and brute force the password. Alternatively we could deauthorise them from their network and manipulate them into connecting to a rogue Wi-Fi device which is controlled by the attacker.
Let’s assume it was transferred via mobile telephone. We know the meeting was taking place at 1120, let’s assume it began at 1100. At 0900 an IMSI catcher is placed near all 35 attendees home addresses with the intention of intercepting traffic between cell towers.
Farfetched you may be thinking? But what secrets could be gained by an attacker using this infiltration technique? Relate this to your own business, it may be worth reconsidering about posting a photo of your meeting online, even if you are only holding a Zoom cocktail on Friday evening from the comfort of your breakfast bar.
Aside from joining the meeting, what other information is unintentionally leaked? We can see that Michael Gove’s name, michael.gove739, appears to what could be an email or a recycled username for other accounts, perhaps his Myspace account I wonder. This isn’t an attempt to breach Michael Gove’s security so I won’t delve into the methods of how that information could be used, hopefully it alerts a reader to consider what information they post online. Just in case member of the Cabinet Office don’t read Twitter and Linked In, I did send an email to the relevant person to inform them of the mishap.
Collaborative applications will continue to revolutionise how we remotely communicate for decades to come, I for one are an advocate of distributed working and will continue to use similar software. Before hosting or attending a meeting, take the time to check the settings of whichever application you find yourself using, default settings are often set for convenience and not for maximum security.Some tips to protect your Zoom meeting include:
• Disable “Join Before Host”.
• Disable “File Transfer”.
• Disable “Allow Removed Participants to Rejoin”.
• Enable “Require Meeting Password”
• Lock the meeting once underway
Before posting anything online, stop and think, meeting IDs are sensitive so don’t share them on social media. Zoom has formed the focus of this article due to their impressive recent growth with an increase from 10 million to 200million daily active users within a 13 month period to date with Microsoft Teams jumping from 32million to 44million within a 24 month period. There have been reports of other platforms being interrupted by unwanted persons, do your research on any application which you decide to use, you are encouraged to be sceptical when your cyber security is at risk. Fear stories usually have an ulterior motive so don’t be discouraged from using any technology, adopt an open mind and clarify any concerns you have; research using the motto ‘trust but verify’.
Many lessons are being learnt and people are adapting to the situation which we found ourselves plummeted into and it will no doubt continue. For those who had to adapt and have been able to operate during this difficult time, this may be the catalyst to enable more distributed working across their organisation, perhaps a few changes to management and resourcing is required but with some careful planning and communication, there are opportunities for businesses to not just survive but to thrive from this experience.
Our work environment is often overlooked yet extremely important, it predicates affective cognition, energy and ultimately, our productivity. For each person to reach their potential they have to shape their working environment with careful planning which is entirely possible when working from home, not so much when working from a communal office where comfort is not the main concern. This can continue if we all embrace technology in a secure manner and use it to stay connected, regardless of the uncontrollable situation which we find ourselves in right now.
Stay safe people,
Best wishes.
Dan